There are many ways to save passwords, but some are safer than others. Let’s talk about how to save and protect your passwords using a password manager.
Why Use a Password Manager
I don’t remember exactly where I was on Amazon the other day when I saw a password book for writing passwords being promoted. How terribly wrong could this go? I couldn’t help myself – I immediately wrote a review:
UpUGo Password Book with Alphabetical Tabs, Internet Address and Password Keeper Notebook for Computer & Website Logins

Just don’t do it!
- What are the chances that someone could steal your passwords if you buy this book? They are great. Your family, your friends, random thieves, etc. How do you get your passwords then? You can’t.
- What happens if a fire or other natural disaster in your house and you can’t get the book out on time? It’s destroyed, and all your passwords are destroyed with it.
- What happens if you take it somewhere and lose it? All your passwords are gone.
The solution is to use an online password manager that you can use on your desktop computer and your mobile devices. It won’t get stolen, burned, lost, or otherwise destroyed.
First, let’s talk about the things to do for password safety.
Use Unique and Strong Passwords
I know using the same password is a temptation because it’s easy for you to remember. But that’s a really bad idea. Using the same password repeatedly means that someone who breaks into one of your accounts could break into others. Even if your bank and credit card passwords are unique, a decent hacker can get to those via one of the reused passwords. I am not going to go into how to do that, but rest assured, it is more than possible.
Do Not Use Passwords that People Can Guess Because They Know You
Don’t be tempted to use something like your Grandmother’s name and your child’s birthdate for a password. People who know you will know your grandmother’s name and your child’s birthdate. We have all seen this on television and movies, where the hero of the story has to break into someone’s computer and is with the person’s friend or family member who can answer pertinent personal questions, and the hero gets into the computer, safe, or whatever they need to get into. Fiction imitates real life.
This movie was made in 1983, and David was able to guess the password “joshua” because he knew Professor Falken had a son named Joshua.
Don’t Answer Quizzes on Social Media
Quizzes on social media are popular, both for the users and the bad actors. When quizzes ask about your favorite vacation spot, your childhood pet’s name, the most recent book you liked, etc., that is to gain information that can be used when security asks questions to identify you. If a hacker has your username and password that they got from the Dark Web and has that information, boom, they’re in!
Use 2FA Where Offered
Yup, it’s a pain in the you-know-where when you have to grab your phone to get a code sent to you. But it’s the safest thing to do. If you are on your Windows computer a lot and your phone is in another room, you can use Microsoft’s Phone Link on your Android or iOS phone. Apple has its own way of linking from an iOS phone to an Apple computer.
Yes, some security issues exist with some forms of 2FA, especially those that send an email. If you are sent an email with a code and someone else can access it, they will have that code. Email is not very secure. A text message is a little more secure, but an authenticator app is best.
Please be careful when choosing an authenticator app. Note that plenty of apps in the app stores that look like genuine authenticators but are not. I recommend Authy because it is cross-platform, easy to use, and free. I don’t recommend Google. Google has already been caught with its pants down tracking user data in what was supposed to be private mode.
Use Passwords that Make Sense but are Still Strong
How do passwords get hacked? There are several ways, including breaches where thieves sell stolen usernames and passwords on the dark web, social media, and brute force. Brute force means a computer keeps on guessing until it gets through.
One of the best ways to make a strong password is to string some words together; for example, eagles are big birds. Please don’t try to use any of the following for your password. I’m sure bots have already come along; this is for demonstration only.
If you run the password eaglesarebigbirds in a password checker, it will tell you a brute force attack by a computer could crack the password in 3 hours.
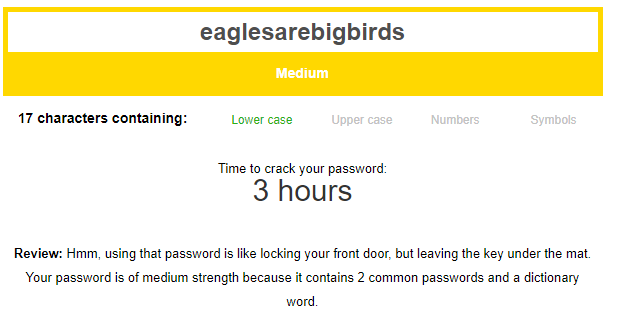
So, how do you turn that into a password that meets the common criteria of an uppercase letter, a number, and a special character? It’s actually pretty simple:
- Eaglesarebigbirds – the E is capitalized
- Eaglesareb1gb1rds – i has been replaced by a 1
- E@gles@reb1gb1rds – a has been replaced with the @ sign
- E@gl35@r3B1gB1rd5 – e has been replaced with 3, s with 5, and the Bs are capitalized
Now let’s see how it is with those improvements:
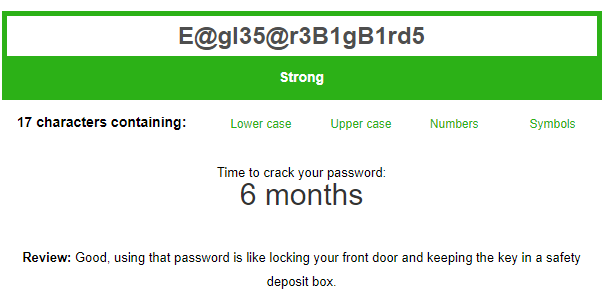
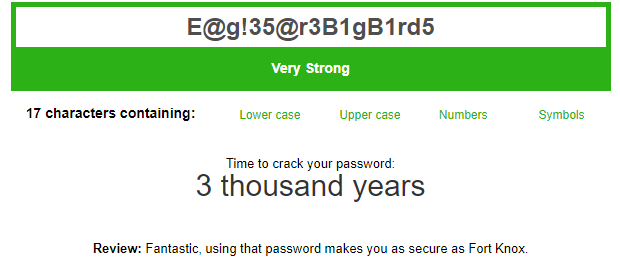
Well, that’s fantastic! But, you know what? We can make it even stronger by replacing the l in eagle with an exclamation point !, so it becomes E@g!35@r3B1gBird5.
Use a Password Manager
So now that you have a nifty, strong password that can’t be cracked for 3 thousand years, where do you save it? You save it in a password manager.
The best thing about using a password manager is that you don’t have to remember or write your passwords. The manager remembers them for you, and good password managers, like Proton Pass, will recommend passwords for you. All you need to remember is a master password.
Now, you may ask how to save that master password. You could try my method. I have a contact that doesn’t exist, but I can reach the information on my phone. I have my most important password saved as a note for someone who doesn’t exist. Even if someone were to hack my account, they would have to go through all my contacts, and even if they did find that contact, they would still have to do some sleuthing to get the information.
Why We Recommend Proton Pass
We recommend Proton Pass for several reasons:
- It is used by journalists and others who need to keep their information secure.
- It has never been breached.
- It’s made in Switzerland so you know it’s gotta be good.
- They have a free version which should be suitable for most people.
- It’s easy import your passwords from Chrome or another browser. The advantage here is that you are no longer in a walled garden where Google is gathering information about you to sell to third parties.
- It’s cross-platform meaning Proton Pass will work as an extension to your browser, and will also be available to you on your mobile devices.
- Proton Pass is also cross-operating system compatible for Windows, Android, Linux, iOS, and Apple.
- Proton Pass is open source which means that anyone can look at their code and determine that they do what they say they do, nothing more, and nothing less.
- The icon is purple, my favorite color!
We’re Here to Help
If you would like help installing and learning how to use a password manager like Proton Pass, please feel free to contact us.

